Anonymization and Zero-Knowledge Proof
All transaction information is made public while meeting the following requirements to protect privacy (anonymizing the trader) at the same time.
Requirement
For the trader himself/herself to display the fact that the transaction had taken place without a third party and also without disclosing the trader’s own private key
Inability to determine the trader from transaction history or from the combination of transaction history
Low cost
Should the original ID of the trader who has completed the transaction is recorded, it will become possible to determine every past transaction conducted by this certain trader. Therefore, the focus was to find ways to provide the transaction history of a certain trader which history can be traceable to this certain trader but without recording the trader’s ID. Now, this is a potential privacy issue regarding Ethereum’s wallet address and its transaction history. But since the technology already offers a solution, it has advantages other than operational speed when compared to an all-on-chain implementation.
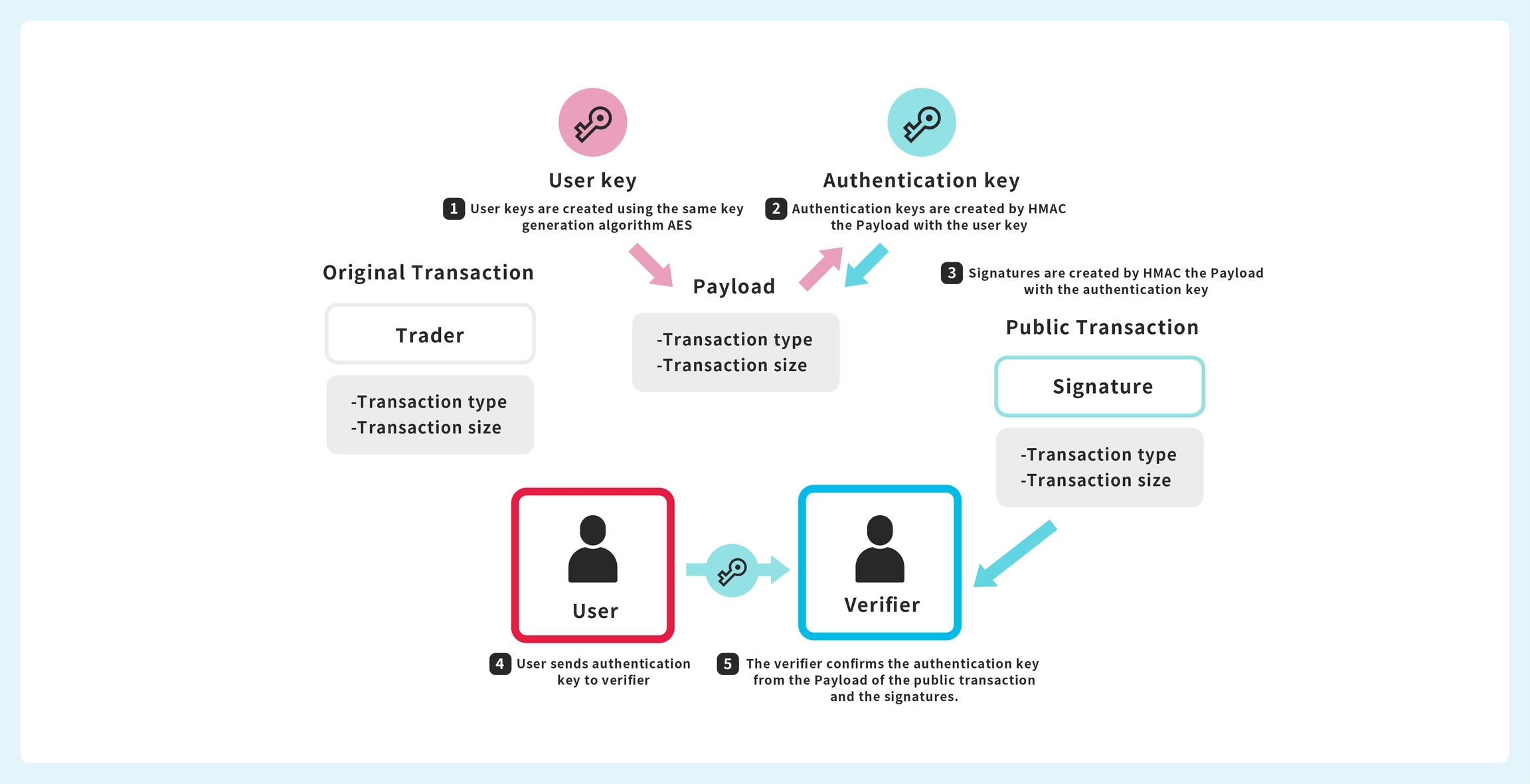
To meet the above requirements, a zero-knowledge proof model is adopted.
The following is an overview of the model.
From the payload of each transaction, a signature key (private key) is generated by using a different private key for each user. This key will be generated for each transaction.
A signature key is used to sign the transaction, which is then published with the content of the transaction.
If you want to prove to a third party that you are the trader of this transaction, present the transaction log published with the signature key of the corresponding transaction. The verifier confirms that the signature key received is identical to the signature.
Displayed in the diagram below.
Last updated